


Next: Miscellaneous Issues
Up: Security Analysis
Previous: Smart Cards
Its very difficult to design protocols for security usage. Large research has been done in this but still designing in new scenario and for new systems always comes with interesting vulnerabilities.
How does the simputer authenticate the smart card and vice-versa? As the device is nascent their has been no soluiton to my knowledge. Here I propose the following authentication of the smart-card(SC) and the device(D) based on GSM mobile phone system[And01c]. Note that simputer support PGP-like public key cryptography security mechanism in general and it may have more than one users and corrresponding data areas. The key computations are done by Smart Card (as Crypto Processor).
- For each user the smart has a separate data area one highly secure with users sensitive information and pin.
- The user presents its pin(PIN) to the device. The device gives it to smart card which authenticates the users.
- Once the user is authenticated(User Valid) the device must be authenticated to be able to read sensitive information from the smartcard.
- The device sends its name(serial number
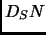 ) encrypted in its public key(
) encrypted in its public key(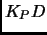 ). The smart card sends this with a nonce(N), name of device and users public key(
). The smart card sends this with a nonce(N), name of device and users public key(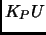 ) all encrypted in users private key(
) all encrypted in users private key(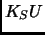 ) to the certifying server(CA). Along with users plain text public key to the device which forwards it to the authenticating server.
) to the certifying server(CA). Along with users plain text public key to the device which forwards it to the authenticating server.
- The authenticating server sends the authentication (GoodD or the Nonce N) encrypted in users public key. Thus the smart card authenticates the device.
- To make the process faster the smart card also keeps a cache of authentic device key , serial number and expiration time stamp.
The protocol:
In BAN [Bur92] Logic:
| (SC believes good User) and (SC believes CA said good Device) |
| SC believes good Device |



Next: Miscellaneous Issues
Up: Security Analysis
Previous: Smart Cards
Vaibhav Bhandari
2001-11-29